Clickjacking
Clickjacking is a fraudulent method that can be used, for example, to collect website users' personal data without their knowledge.
Visitors on a site that uses clickjacking may subscribe to something in a social network or “like” a posting without even noticing it. The site then automatically determines what the user's account is, and its owner can use the account personal data. For example, the phone number can be used to make annoying sales calls and offer products to buy. This mechanism is most often used in services that “increase sales”.
If clickjacking is detected on your site, we recommend that you stop using it. You don't have to refuse a service wholesale if it offers clickjacking along with other techniques. It's enough to turn off clickjacking. However, please note that clickjacking is a fraudulent method and you should pause to think if services that offer this technique are trustworthy.
How do I find clickjacking on my site
Clickjacking is typically implemented on the site by creating hidden elements that interact with social networks. As a rule, elements are placed on top of buttons, forms, videos, and so on. They can also move around the page following the mouse cursor. These elements are not visible to the user, but they can be found in the HTML code of the pages.
To find clickjacking on a site, you need to identify the code fragments that create hidden elements. To search for them, you need to log in to the social network and use the browser console.
We recommend using browsers such as Mozilla Firefox and Yandex.Browser, Google Chrome, Opera. The browser console is usually opened with the keyboard shortcut Ctrl + Shift + J, as well as Ctrl + Shift + K when working with Mozilla Firefox. For the Apple operating systems, ⌥ + ⌘ + J and ⌥ + ⌘ + K shortcuts are used.
Below is an example of working in the Mozilla Firefox web console when logged in to VK.
- Log in to the social network. If you can't do this, it may be impossible in some cases to use this algorithm to detect clickjacking.
- Select a site page to check for clickjacking.
- Remove site cookies in the browser.
- Open a new tab in the browser.
- Open the browser console. Then enter the page URL in the address bar. Wait for the page to load, imitating the user's activity: move the mouse, scroll the page.
Identify the site's requests to social network URLs.
To search in the console, go to the Network tab and find the social network URLs used for the “authorization” and “like” events. For example, in Vkontakte the “authorization” event corresponds to the URL path widget_auth.php, the “like” event corresponds to widget_like.php.
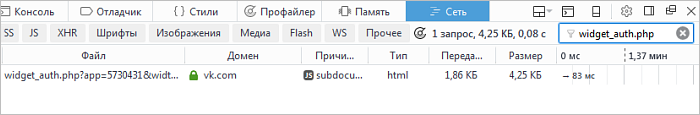
If you can't find such social network URL, there was no clickjacking attempt. It's possible that you already deleted the clickjacking code from the page, or that you can't reproduce the clickjacking attempt with this algorithm.
Identify the code that invokes the loading of the hidden site element.
To search, go to the Inspector tab. Find the HTML elements that match previously specified social network URLs.
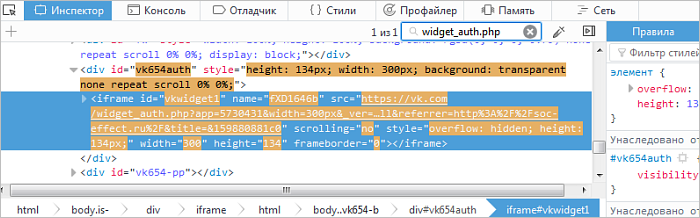 Then check each identified element to see if it's responsible for the hidden or visible part of the website. To check, hover the mouse cursor over an element. Its area will be highlighted on the website page. The element can be located in an invisible part of the screen. To find it, right-click on the element. In the context menu, select Scroll to view.
Then check each identified element to see if it's responsible for the hidden or visible part of the website. To check, hover the mouse cursor over an element. Its area will be highlighted on the website page. The element can be located in an invisible part of the screen. To find it, right-click on the element. In the context menu, select Scroll to view.If the website element is hidden, most likely, you found clickjacking. Go to the next step.
Note. If you didn't find the code fragment in the Inspector tab, but there are requests to the social network at the URLs specified above in the Network tab, you detected clickjacking.Detect the code that invokes interaction with the social network. Pay special attention to the script, iframe or object elements.
If an element isn't found, you can identify it by removing code fragments that raise doubts one by one. After deletion, repeat steps 3 through 8.
When you make changes to the website, use the I fixed it button on the Security and violations page in Yandex.Webmaster to inform the robot of the actions you completed.
You can click the I fixed it button again for the same site after a month. Further, this period is increased up to three months to avoid the button misuse. Therefore, we recommend using the button only when you are sure that there are no more violations on the site.
If multiple users have website management rights in Yandex.Webmaster, agree on who will send the website for re-checking and when. After clicking the button, none of the users will be able to click it again within a month.
Frequently asked questions
I deleted everything. When will restrictions be lifted?
The restrictions are usually lifted within two weeks after you eliminate the violations. If the robot detects clickjacking on the site again, the restriction period may be extended.
I'm sure I don't have any clickjacking on my site, what should I do?
We recommend checking for clickjacking using the instructions posted above. After the check, click I fixed it on the Security and violations page. If the site doesn't use this technology, the restrictions will be removed.
I did everything, but the restrictions aren't lifted
Make sure that the site doesn't contain any program code used for clickjacking. There could be several services used on your site that may offer clickjacking.
Make sure that enough time (more than two weeks) passed after clicking the button. Otherwise, Yandex algorithms may not have tracked the changes on the site yet.