Private server attacks
The article "Modern Internet attacks" is provided by Sophos Plc and SophosLabs.
August 2007
Not all Internet attacks use compromised sites. Every day numerous specialized malware sites appear on the web. The domain registration procedure is hardly controlled, which allows to create sites for Internet attacks or traffic interception from similar domains. The latter method assumes creating a site with a domain name similar in spelling to the an existing site. Such methods are commonly used for phishing, but are not limited to it. We can't say that the names of domains for attacking sites follow some certain rules. In some cases they use normal respectable-looking names, in other cases they use senseless and often unreadable sequences of characters. Attacking sites can also be created using free hosting services, without registering a separate domain. When identifying the attacking sites it is important to check the domain registration information to determine whether the site was deliberately created as malicious. In fact, we need to answer the question if it is compromised or attacking.
Two recent cases can serve a good example of attacks that use well-known names. Both attacks used fake Google domains to infect victims. The first site disguised as a localized Google search page [48] but in fact it contained the code infecting victims with malware. In the second case, a site disguised as a web counter service tried to exploit several vulnerabilities in various browsers (including MS06-057 [49], WinZip, MS06-055 [50], QuickTime (CVE-2007-0015) and MS07-009 [51]) to install malware. Curiously, a subsequent attempt to access the second site led to the regular Google search page.
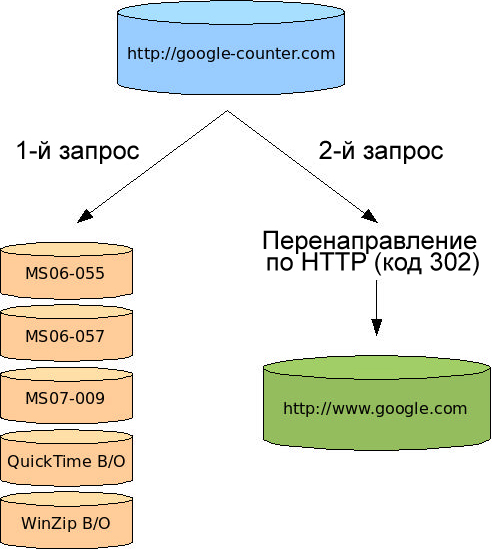
Fig. 11. An example of an attacking site that exploits a vulnerability to infect the victim at the first visit and then simply redirects it to the Google search page.
The popularity of ready-made and openly distributed tools for creating malicious driver-by sites has grown lately. Two of the most famous examples are MPack [52.53] and IcePack [54], widely used in Internet attacks throughout the year 2007. Such kits are relatively inexpensive to purchase on special Internet forums. They include a set of PHP tools for creating attacking sites. Buyers can use such kits to create malicious sites using numerous browser vulnerabilities and infect victims with the chosen malware. They don't need to have experience in developing scripts and exploits. With this kit you can also create a landing page from where the malware is spread. After that, the hacker just needs to attract visitors. Usually it is done with spam or compromised sites. Once such page is opened in the browser, the script starts trying various exploits to infect the victim. Often such kits support updating. When a new vulnerability is detected in any browser the landing page is updated to increase the chance of a successful attack.
Information about victims is recorded in the database, which lets the hacker track the attacks success rate. Such statistics is also used to avoid repeated attacks on prominent clients. Repeated query returns a blank page or a harmless message (for example, ": ["). Some kits even use a script disguised as a "Sorry! You IP is blocked." message (original spelling preserved).
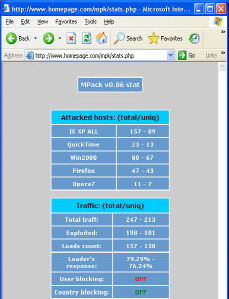
Fig. 12. Example of a statistics page on an attacking site created with the MPack package.
If a site was created and configured for attacking, the hacker needs to attract victims to it. Usually two methods can be used: hidden download of malicious iframe tag imbedded into the compromised site, or spreading the site link in spam messages. Social engineering methods used in spam usually rely on pornography, for example offering a porn photo or a video with celebrities [55,56]. In several of the recent attacks, the users who clicked the link received malicious Iffy [57] script which uses a number of browser vulnerabilities to install malware. The first attack with Iffy used special malicious ANI files aimed at the recently revealed Microsoft Internet Explorer vulnerability of animated cursors. Subsequent Iffy attacks used other exploits apart from MS07-017 to infect their victims.
Iffy is a good example of a script used in various attacks to install malware. In 12 hours used to write this article, SophosLabs revealed 10 new Iffy attacks (see Fig. 13). They installed malware from three different families, their files were constantly updated with the means of server automation (see Table 1). One attacking site was used to load a landing page of another attacking site created using IcePack kit, which in turn created a new infecting mechanism. These examples are not complicated or unusual. They use methods applied in majority of modern web attacks.
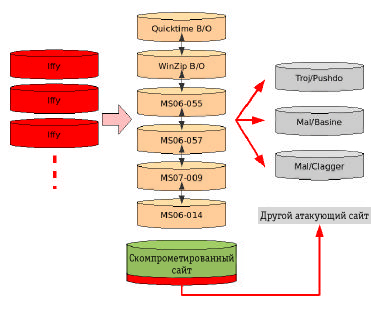
Fig. 13. Review of infecting mechanisms in Iffy attacks registered during 12 hours. In each attack, Iffy script was used to infect victims with a malware representing one of three famous malware families. One of the attacks used Iffy to load the page of a separate attacking site created with the IcePack kit.
The most popular way to redirect users to landing pages created with PHP sets is embedding a malicious iframe tag in the attacked page. This allows to configure one attacking site visited by victims of compromised sites where they get seamlessly loaded malicious script. Such attacks use a combination of specialised attacking sites and several compromised sites where users are exposed to attack. The side effect of using several compromised sites is that even after the final attacking site becomes unavailable compromised pages still try to request malicious content.
On of characteristic features of malicious scripts has always been that they can be quickly adapted for using a new vulnerability. As a result, they develop a lot of small variations that people copy and make minimal changes. A similar situation is seen in the case of Internet distributed PHP tools: there are many attacking sites that host scripts similar to those created using such tools. Probably, it is the result of manual copying in attempts to save money on acquisition of such tools (the price is usually several hundreds of US dollars).