Malicious sites
The article "Modern Internet attacks" is provided by Sophos Plc and SophosLabs.
August 2007
Malware can be located on various sites. Hackers can use free hosting services, create new sites designed for attacking, or capture existing sites, turning them into a base for attacks. In most cases, they use scripts (usually JavaScript) to infect the victims. Common scripts often call the client browser to ensure the correct display of pages. Malicious scripts can call the browser to load a suitable exploit. Usually the script iterates through the list of known exploits to find the one from which the client is not protected. Simplified pseudocode of the attack is shown in figure 7. Of course, real malicious scripts use a variety of tricks to mask their content and avoide detection. Hackers use new exploits as they discover new vulnerabilities (for example, a recently found new ActiveX exploit for Yahoo! web camera control elements [30]). The information about using vulnerabilities is publicly available, so creating an exploit becomes a relatively easy task. Furthermore, the code used to exploit the vulnerability in one ActiveX control can be reused for for another control with a minimal revision.
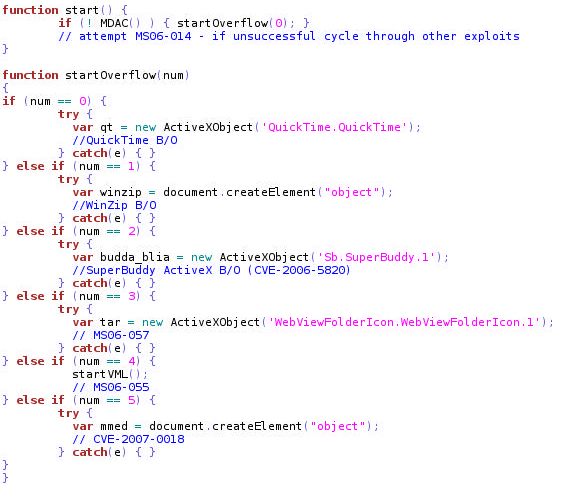
Fig. 7. Pseudocode is a typical modern internet attack.
This section focuses on compromised and infected sites, as well as on the sites specially created for attacks.